Subscribe to join thousands of other ecommerce experts

How advanced is data protection in 2021? Does your modern browser respect privacy and therefore not forward any personal data to unknown third parties without your consent? The short – but still true – answer is: no. The longer answer is: it depends. What is for sure though is that the situation is rather confusing, even for individuals with a technical background. Therefore, I did some research on the topic of browser data protection in 2021. In this blog I am going to share with you the key findings.
Table of Contents
Observation 1: Data protection is an issue today
Nowadays, privacy matters have become part of our daily routines. Clicking away a cookie consent dialog is part of today’s user experience, and not the best one. The GDPR (General Data Protection Regulation) created new business models, such as consent management platforms. Supporting the GDPR principles is essentially a sine qua non for larger SaaS vendors now. As a matter of fact, privacy concerns are mainstream in 2021.
However, how does your main tool – your browser – handle privacy for your various internet experiences? Moreover, what is the situation on your mobile, where many apps are just thin wrappers around something called web views, which in fact are just browsers again? In a nutshell, it’s a disaster. It always was.

Observation 2: Browser vendors are taking action
Probably, for this reason, browser vendors decided to take some counter-measures to prevent information from leaking. I will give you some examples: In 2017, Apple introduced and added Intelligent Tracking Prevention to the Safari browser, blocking 3rd-party cookies used for cross-site tracking. This came as a despair of ad tech land and others, whose remarketing endeavours are usually based on third-party cookies. Fingerprint defence was also announced to prevent misuse of your personal information, which is good in theory but not a perfect solution yet. For more information regarding this development, I highly recommend reading this article published in the Financial Times.
In 2019, Google announced its new privacy strategy, which you can find here. Just like Apple, they’ve introduced better fingerprinting defence. However, concerning cookies, Google proposed a different approach: more control over 3rd-party cookies. No surprise there, since Google has a far greater interest in cross-site tracking data than Apple.
In contrast, Mozilla’s Firefox browser offers a lot of control over privacy-related features, an in-detailed explanation of which can be found in this blog post. This is probably one of the reasons why the Tor browser is based on a stripped and adapted version of Firefox.
Observation 3: Third-party cookies are (sometimes) evil
Since February 2020, some technical users might already have noticed a new warning message in the developer console of the Google Chrome browser. It goes like this:
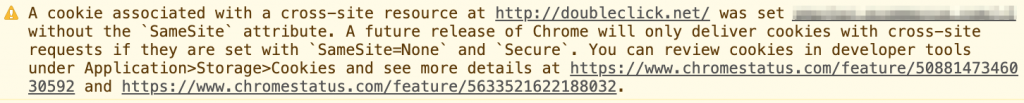
This is because Google Chrome 80 has already implemented a new standard proposal for a more fine-grained 3rd-party cookie control. In my example above concerning Doubleclick, which is ironically a Google company, third-party cookies would be blocked by future versions of the Google browser. So I guess they will be changing that rather soon.
This SameSite proposal – cookie classification, secure by default – is less harsh than Apple’s blocking approach. Both methods can prevent a very common abusive attack known as CSRF.
Observation 4: The dark art of browser fingerprinting
Now here is the real deal everybody should be talking about: browser fingerprinting. And this is nothing new, it was always here and I would bet, it has always been used. Without anyone noticing. Without anyone’s consent.
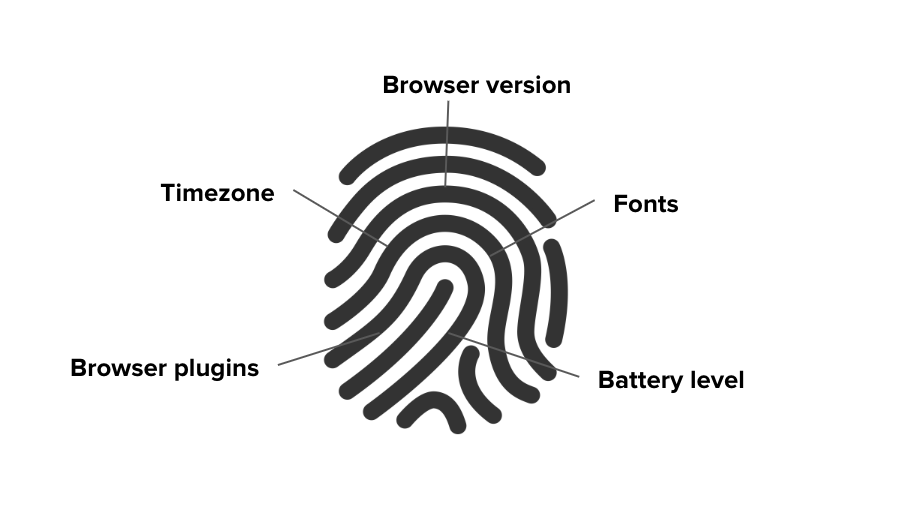
Browser fingerprinting may take some explaining. As a starting point, I can recommend the following blog post by the Washington Post. The basic idea is to combine all the information your browser is exposing (usually for good purposes such as installed fonts, battery status, etc.), apply some set theory, and calculate a unique value for your browser environment, and by extension, you.
This is why every browser vendor is proposing fingerprinting defence as a future strategy to protect privacy. Is it an easy implementation? Absolutely not. In this Tor project blog post you can take a look at the current state of research and learn which problems exist that need to be solved first.
Furthermore, you can get a hint of your online uniqueness by visiting test sites such as this open source project. Don’t forget to try it out on your mobile, as well as a desktop browser.
Conclusion
As this blog’s title suggests, browser data protection is complicated. The privacy threats mentioned above are not genuinely new, as we have been dealing with 3rd-party cookies for the past 25 years now. Moreover, it is not only about web browsers but also about your mobile environment, as apps make quite some use of integrated mobile browsers. Currently, the major issues are being addressed by browser vendors, but this is rather a slow process: New standards need to be established and entire business categories are at stake, as there are companies who sell and track user profiles.
Protecting your privacy today is hard, even for tech-savvy persons. Third-party cookies are occasionally useful and at least you can delete or block them – nevertheless, browser fingerprinting is a real problem. So if anyone complains about 3rd-party cookies, just explain fingerprinting and show some demo pages of this dark art.
All in all, my recommendation here is to take your privacy very seriously and to keep yourself informed and aware. Most importantly, you should not rely on your privacy being respected on the internet, whether searching your browser or using seemingly innocent apps on your mobile or other devices.